It started with an early Sunday morning phone call. A senior equity partner who writes whenever and wherever inspired complained, “I’m getting an error whenever I try to open Word or PDF documents.” Two hours, and a trip into the office later, we erroneously concluded our case file folder had been corrupted from an unsuccessful backup and a simple scan/repair job would have us back up and running.
Unfortunately, while the scan/repair utility sifted its way through 1.5 terabytes of files, a more destructive tool was worming its way through our network shares as well. It wasn’t until another partner emailed late Sunday evening to inquire about strange file names like “HELP_DECRYPT” saved in his case directory did we realize we had a more serious problem on our hands. We’d been struck by the CryptoWall 3.0 ransomware virus! (Que Scary Music!)
What is CryptoWall 3.0?
“CryptoWall is “the largest and most destructive ransomware threat on the Internet “at the moment and will likely continue to grow.[1] Essentially, CryptoWall, an evolution from CryptoLocker, uses malware to copy and encrypt commonly used office file extensions, then deletes the original, leaving victims little or no options beyond paying a ransom or losing the ability to recover their files. In a law firm, losing client data, past and present, simply isn’t an option. In our case, the ransomers wanted $700 to supply the key to decrypt our files! Though we had roughly triple that amount in lost productivity and billable hours fixing this mess, negotiating with terrorist simply wasn’t an option! However, fortunately, if your organization has a cold backup the likelihood of recovery drastically increases.
When we investigated just how much the virus purveyed through our network, we noticed it was centralized in the heart of our operation, client case files, and law firm application data shares. Though we knew we had cold back-ups to restore from, we didn’t know if the virus had stopped spreading or even know where it originated. The last thing we wanted to do was to restore our files only to have them encrypted all over again!
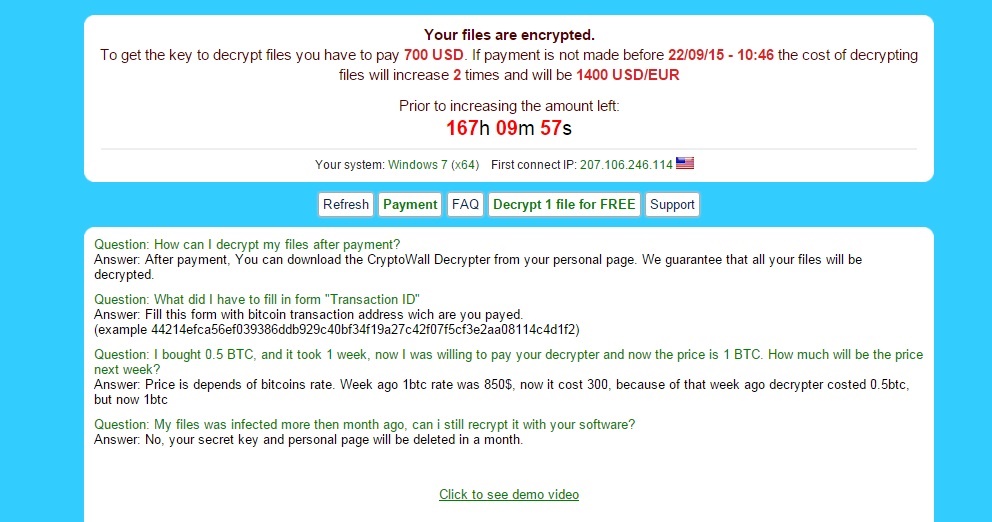
Identifying the Source of the Virus
Once you notice your organization has been affected by CryptoWall, some engineers suggest you power down your network switch to prevent spreading. While this works for smaller networks, it may not be feasible, especially for larger organizations. I would simply suggest modifying share permissions to critical shared drives to prevent infected machines from writing to those drives and further spreading. Unfortunately, there is no administrator level method to determine which machine the virus originated from. I had to walk around to each and every machine in the law firm, install, and run applications such as MalwareBytes, Hitman Pro and ListCWall to scan, identify, and remove any locally infected files. Once we identified the source of the virus (HELP_DECRYPT files will appear locally), I scrubbed it clean and proceeded to delete and restore our files.
Restoring the Infected Files
There is something unnerving about deleting 1.5 terabytes of client files even when you know there is a backup, but it was necessary. Besides, all of it was utterly useless encrypted garbage at this point. After deleting, we used an application called Karen’s Replicator to replicate the cold backup drive to the previously infected share drive. It took approximately 2 days to restore 1.5 terabytes worth of data, but it worked, and so far, so good.
We also noticed that QuickBook files, both current, and backups were affected as well. Luckily, we were able to restore company files from previous routine bare metal Windows Server Backup.
How You Can Protect Your Network
The bottom line is this can happen to anyone. One erroneous click on the Internet, opening an attachment from even a trusted source whose email contacts have been compromised can unleash a world of hurt on law firms who increasingly rely on sensitive client data to operate. The more we embrace technology, the more vulnerable we become to it. Keeping end-users up-to-date with safe browsing practices is a start. TechRepublic has some great tips for keeping your network safe and avoiding the likes of CryptoWall 3.0.
[1] CryptoWall ransomware held over 600K computers hostage, encrypted 5 billion files, PCWorld (2014), http://www.pcworld.com/article/2600543/cryptowall-held-over-halfamillion-computers-hostage-encrypted-5-billion-files.html (last visited Sep 22, 2015).